root@hckrt: ~#
Managed Bug Bounty Program
Security threats are evolving, while organization's IT systems and applications are constantly changing. System downtime can be expensive; a hacker attack can even destroy the reputation of the company in minutes. Therefore, organizations must test their IT environment regularly.
A bug bounty is about using the power of crowdsourced security to protect your business. During a bug bounty program, a company can offer rewards to ethical hackers for reporting vulnerabilities.
The bug bounty program is a proactive way to secure your business.
{Main benefits}
Hackrate can help you to go beyond textbook testing methods and find hidden vulnerabilities. Our creative ethical hackers are simulating attacks similar to real life in order to get the most accurate result and find the gaps that can lead to a data breach.
Continuous testing
Penetration tests are time-bound activities, but with a bug bounty program, you can achieve continuous security testing of your product changes. Our experienced ethical hackers are using the latest tools to reveal security holes effectively.
Increase the trust
Prevent potential data breaches by reducing security risks. With Hackrate, you can create a culture of transparency and responsibility by actively improving your security level, which means a strong commitment to security.
Centralized view
Our secure platform helps you to keep vulnerability reports centralized and easily manageable, while you can access the identified security vulnerabilities immediately. Our built-in dashboard even allows you to track the bug bounty budget.
Work with the global ethical hacking community
Multiply your security capabilities, not your headcount.

Actionable findings
Fast, validated, and ready to fix.
Built to match your maturity
Start focused, then expand—without switching platforms.
Bug bounty program in four steps
PLAN
Definition of the scope
Definition of the objectives and requirements, especially what is in the scope, what are the rewards for the reported vulnerabilities, and the number of hackers invited to the program. Our experienced team tailors the program exactly to your needs. We can keep your programs private (with selected ethical hackers) or make your program public (open to our ethical hacker community).
PREPARE
Preparation for testing
Finalization of the testing plan, which contains the timeline and the bug bounty program's rules. For example, what hackers can and cannot do during the testing must be specified, which kind of vulnerabilities are considered accepted. Our team helps you to get prepared and supports you to find the best security testing strategy for you.
TESTING
Testing and reporting
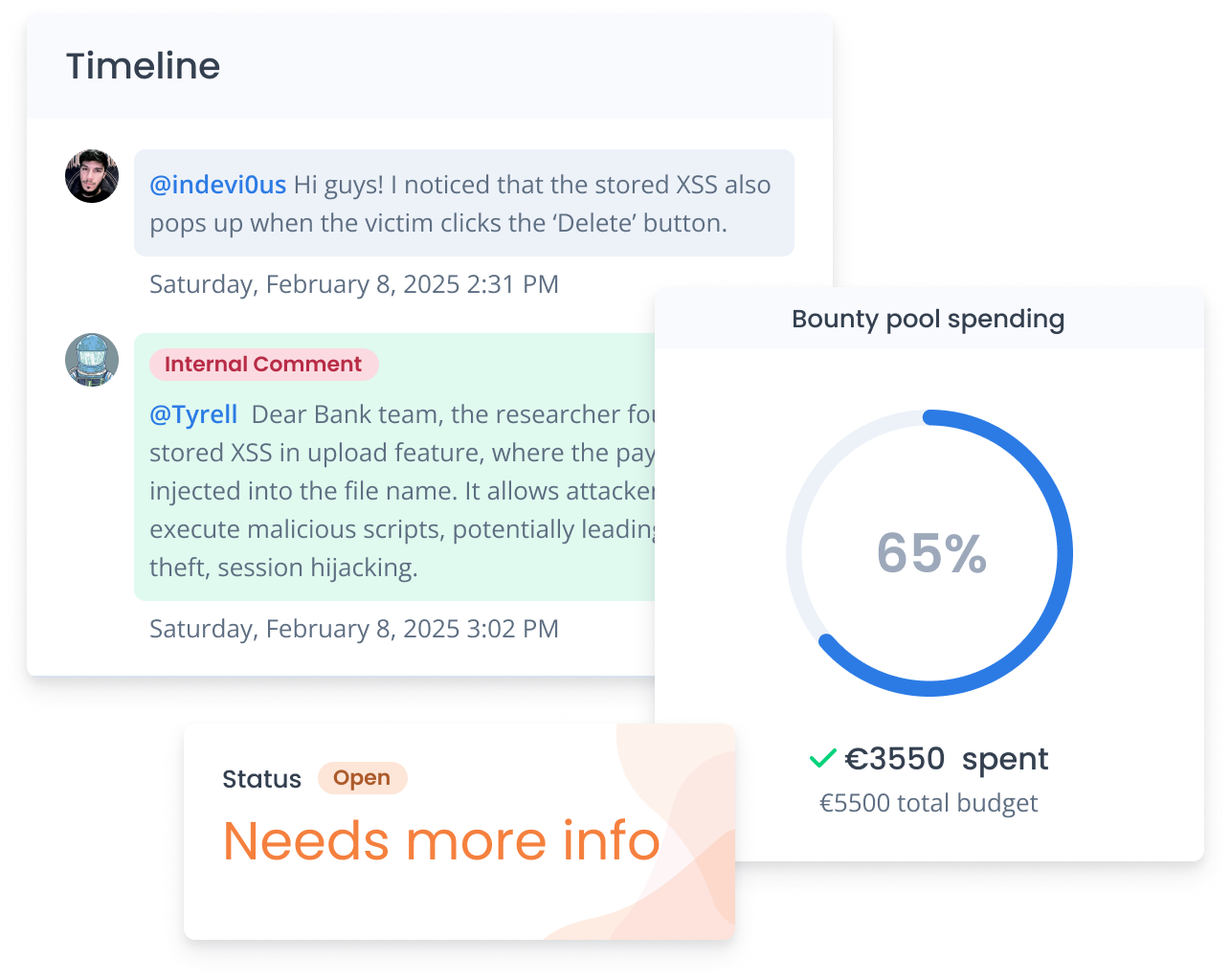
Hackrate launches the program and invites ethical hackers. During the testing, ethical hackers submit bug reports with details on how to exploit the bug. Communication is key in maintaining trust during the process. Our team helps with the communication and verifies the bugs reported by the ethical hackers. Your company receives updates on submitted vulnerabilities immediately via our platform.
FIXING
Remediation of risks
After the validation of reports submitted through our platform, you can start the resolution of identified risks with the help of hackers. With realistic tests of your system's defenses, you will be able to prioritize the vulnerabilities discovered during the tests. Ethical hackers get rewards and reputation points on our platform based on the severity of the identified vulnerabilities.
Ethical hackers think like attackers - not scanners.
Broken workflows, missing checks, and edge cases that scanners don’t understand.
Findings tied to revenue, fraud, data exposure, and operational risk.
Real exploitation sequences across features, roles, and systems.
Reports that auditors and executives can actually use.
Clear structure, consistent severity, and documentation that stands up to scrutiny — without burying teams in noise.
-
1Structured vulnerability reportsConsistent format: impact, evidence, reproduction steps, and remediation guidance.
-
2Severity-based prioritizationTriage that maps to business risk so teams know what to fix first.
-
3Audit-ready documentationEvidence trails and summaries that support compliance reviews and leadership reporting.
Learn more about Managed Bug Bounty Program
Want to know more about Bug Bounty? Download our detailed datasheet today to find out how to proactively secure your business with our Bug Bounty Program.
Proven expertise, recognized by industry leaders.











Hackrate bounty hunters have earned Hall of Fame acknowledgements from some of the world’s most respected technology and financial organizations.
Bug Bounty without suprises
Human creativity. Clear rules.
Full control.
If you want the benefits of the hacker community - without the operational risk - Hackrate’s Bug Bounty programs are built for you.
{Set up your Bug Bounty Program with us}
Start your bug bounty program today and protect your data more efficiently.
Start your BBP todayHackrate
Our platform helps companies to identify software vulnerabilities in a cost-efficient way. It provides a secure and centralized view of ethical hacking projects for your company.
US Patent Applied for HackGATE #63/645,845
Products
From the Blog
-
Press release: Hackrate becomes Hungary’s first CVE Numbering Authority
Jan 13 • 5 min read ★
-
Let 2026 be the year bug bounty becomes part of how you build and operate
Jan 05 • 4 min read
-
Ministry of Regional Development of the Czech Republic Launches Public Bug Bounty Program with Hackrate
Jul 16 • 2 min read ★


Hackrate Ethical Hacking Platform |
2026 ©
![]() Numbering Authority
Numbering Authority