root@hckrt: ~#
Penetration Testing as a Service
It's been proven several times in the past that serious data breaches resulted by unknown vulnerabilities in an IT environment have extreme risk to the entire business.
Are your online services secure enough? How likely is that malicious hackers discover a vulnerability on your product that can ruin your company's reputation?
Penetration testing powered by real hackers, governed like a service. No automation noise. Pure creativity.
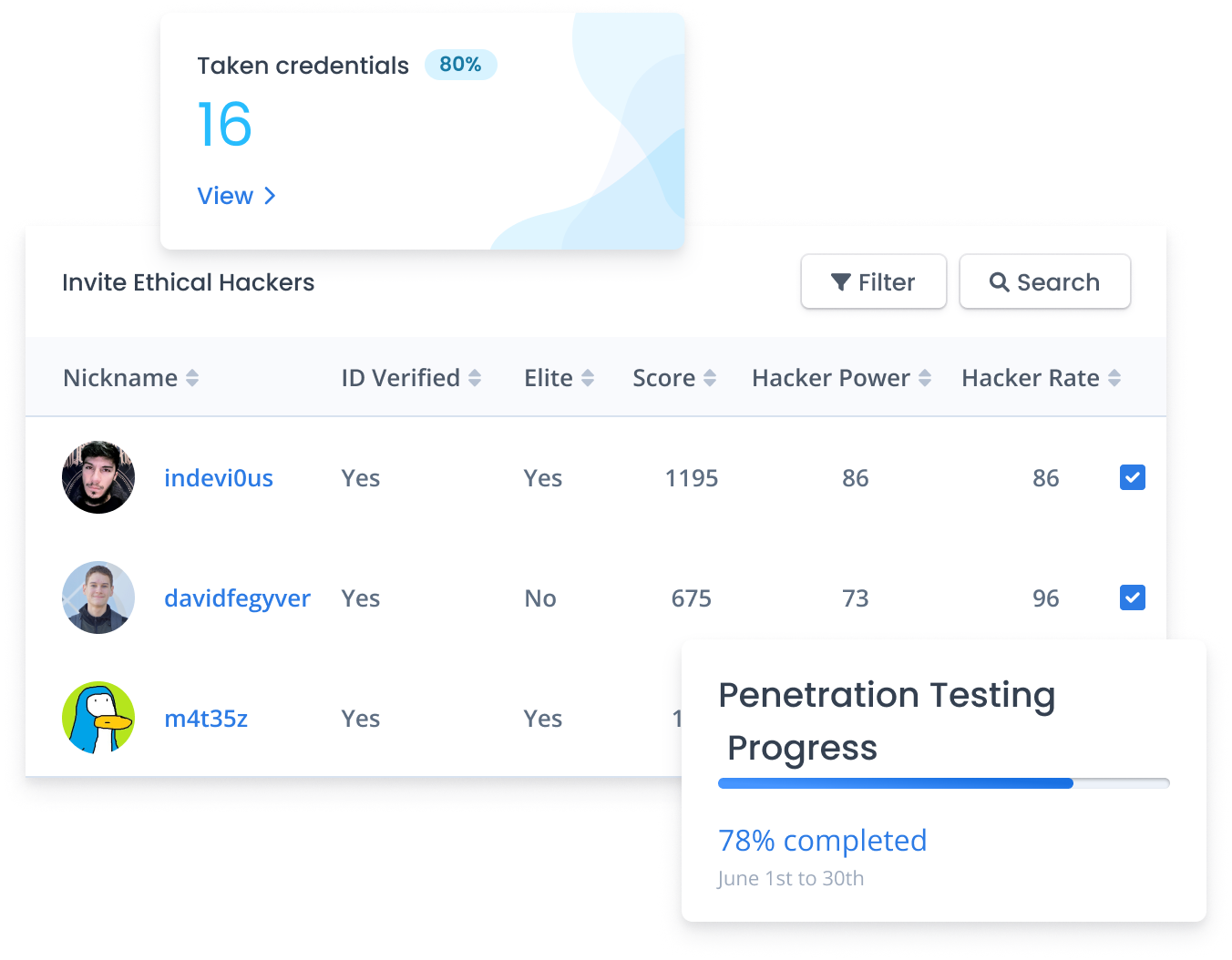
From scope to impact, in days - not months.
The expertise of 5 - 20, delivered at the cost of 1.
Scale your security team instantly - without hiring.

{Why Pentest as a Service?}
In-depth assessment
The global community of motivated, ethical hackers with a more diverse skillset can provide much better results than traditional pentests. Our ethical hackers hold industry-recognized certifications such as OSCP, OSCE, CISSP, and CEH.
Flexibility
With Pentest as a Service, you can choose from a great variety of testing services, from a web app and mobile app testing to API testing. Our team gives you support during the planning process and we make sure that the testing can start within a few days.
Real-time visibility
Access the reported vulnerabilities immediately via our platform. We help you to determine the severity of bugs and we make sure that you only receive accurate reports. With Hackrate, you can keep vulnerability reports centralized and easily manageable.
Ticketing system integration
With our platform, the reported vulnerabilities can be easily added to ticketing systems like Jira Cloud.
Ensure compliance
By testing your security capabilities regularly, we help you to comply with security standards and regulations.
Verified Hackers
To provide a group of selected and verified ethical hackers, we are using KYC verification services.
Designed to support SOC 2 / ISO 27001 programs






Compliance-ready deliverables
Crowdsourced security testing provides a unique method to find your weaknesses and be more secure.
![]() Effective: Our service can be at least two times more cost-effective than hiring external security research to identify vulnerabilities.
Effective: Our service can be at least two times more cost-effective than hiring external security research to identify vulnerabilities.
![]() Confidential: The security testing is an "invitation-only" type of service. Testing is only accessible to a selected group of hackers (usually 4-10 ethical hackers).
Confidential: The security testing is an "invitation-only" type of service. Testing is only accessible to a selected group of hackers (usually 4-10 ethical hackers).
![]() Fast: The suggested length of the security testing is one month, but the first vulnerabilities are usually found within the first few hours.
Fast: The suggested length of the security testing is one month, but the first vulnerabilities are usually found within the first few hours.
Test your application, API, or network for any security vulnerabilities. You can choose from a great variety of testing services:
![]() Web application - Identify vulnerabilities in web applications.
Web application - Identify vulnerabilities in web applications.
![]() Mobile application - Test your mobile assets (iOS and Android devices)
Mobile application - Test your mobile assets (iOS and Android devices)
![]() API - Find security vulnerabilities in your API.
API - Find security vulnerabilities in your API.
![]() Network - Test your network environment.
Network - Test your network environment.
![]() Other - Test for vulnerabilities in blockchain, IoT devices, or desktop applications.
Other - Test for vulnerabilities in blockchain, IoT devices, or desktop applications.
Ethical hackers think like attackers - not scanners.
Broken workflows, missing checks, and edge cases that scanners don’t understand.
Findings tied to revenue, fraud, data exposure, and operational risk.
Real exploitation sequences across features, roles, and systems.
Reports that auditors and executives can actually use.
Clear structure, consistent severity, and documentation that stands up to scrutiny — without burying teams in noise.
-
1Structured vulnerability reportsConsistent format: impact, evidence, reproduction steps, and remediation guidance.
-
2Severity-based prioritizationTriage that maps to business risk so teams know what to fix first.
-
3Audit-ready documentationEvidence trails and summaries that support compliance reviews and leadership reporting.
Learn more about Pentest as a Service
Want to know more about Pentest as a Service? Download our detailed datasheet today to find out how to manage your security tests and be sure that your company is secure.
{Start your pentest project with us}
We help you to set up appropriate defenses for your company.
Start your PTaaS project todayHackrate
Our platform helps companies to identify software vulnerabilities in a cost-efficient way. It provides a secure and centralized view of ethical hacking projects for your company.
US Patent Applied for HackGATE #63/645,845
Products
From the Blog
-
Press release: Hackrate becomes Hungary’s first CVE Numbering Authority
Jan 13 • 5 min read ★
-
Let 2026 be the year bug bounty becomes part of how you build and operate
Jan 05 • 4 min read
-
Ministry of Regional Development of the Czech Republic Launches Public Bug Bounty Program with Hackrate
Jul 16 • 2 min read ★


Hackrate Ethical Hacking Platform |
2026 ©
![]() Numbering Authority
Numbering Authority